Everything You Should Know About Server-Side Vs. Client-Side Rendering
Posted on February 18th, 2021 by Jimmy Rodriguez in Tech, Guides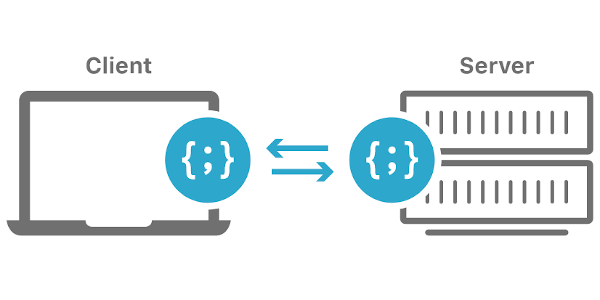
Websites have evolved a lot since the first sites went online almost 30 years ago. We can now shop, interact, and engage with companies from our screens. Along with customers' online habits, the way browsers render HTML has also evolved. In the earlier days of the internet, server-side rendering was the standard way to get the HTML on the screen. Many sites still use it.
How To Determine The Optimal Website Hosting Bandwidth
Posted on December 22nd, 2020 by Richard Conn in Tech, Guides
Running a business in 2020 requires that you have a digital presence. Building a website is one of the first tasks of a new business's checklist. With that comes registering and buying a domain, website design, web development, and paying for hosting.
The Future of 5G and Website Monitoring
Posted on October 14th, 2020 by Beau Peters in Monitoring, Tech
5G. You've likely heard a lot about it passing, but what kind of impact will the fifth generation of mobile technology have on your ability to provide a sturdy, fast website? What does this new tech mean for you?
How Artificial Intelligence is Shaping the Industry of VPN
Posted on July 13th, 2020 by Lianna Arakelyan in Tech
Artificial intelligence refers to the machine's ability to learn and think. Given that it sort of mimics how humans think and reason, AI's application is virtually endless. AI reduces human error, do a task that is risky for humans to do, help humans solve complex, and so much more.
Why Every Company Needs Email Round-Trip Monitoring
Posted on June 17th, 2020 by Andrew Wilson in Monitoring, Tech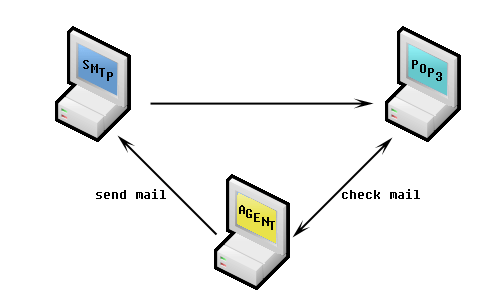
The world of email security is experiencing a boost with the emergence of new technologies. Now, you can monitor and evaluate the whole trip your email makes from your outbox to the recipient’s inbox. Not particularly sure how? No worries! We are here to cover everything you need to know about email round-trip monitoring. Also, we will explain why every company (despite the industry they are operating in) should implement email round-trip monitoring.

 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.