If you watched Mission: Impossible- Rogue Nation, you probably remember the infamous Gait Analysis access control system. After the agent passes through the main gate, enters the elevator with fingerprint recognition, and opens three unique combination locks, he proceeds through a camera-based system that recognizes his gait, speech, and facial movements.
Although this system is the fruit of the screenwriters' imagination (as far as we know!), all the previous access control steps are based on real-life examples.
Access control is a system that restricts access to specific parts of a company. This system involves determining who has access to what, establishing clear rules, and tracking access for authorized individuals. Before granting access to confidential information, individuals must be identified and authenticated.
Organizations use electronic access control systems to safeguard facilities and track employee access to restricted areas, such as data centers. These systems employ user credentials, card readers, audits, and reporting mechanisms. Some systems also feature access control panels, alarms, and lockdown features to prevent unauthorized entry or unauthorized actions.
When designing an access control system, numerous variables are considered, such as the level of control desired, the responsibilities of an IT manager, and how to decide which personnel have access to which resources.
Importance of Access Control Systems
Access control is a crucial component of a security program that helps protect sensitive information, such as client data.
Most businesses have methods and procedures to prevent unauthorized access to networks, computer systems, applications, files, and sensitive data.
Access control solutions can be challenging to administer in setups that include both on-premises systems and cloud services.
Due to high-profile data breaches, some IT companies have shifted away from single-sign-on systems and toward unified access management, which restricts access to both on-premises and cloud environments.
There are many access control models, each with pros and cons. However, when talking with cybersecurity consulting firms, three of them are most commonly mentioned.
Discretionary Access Control (DAC)
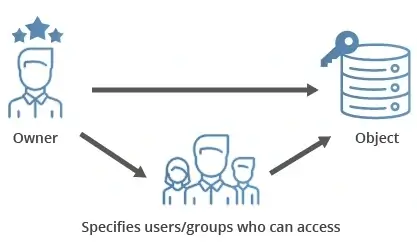
The discretionary access control system (DAC) provides more control to business owners. Even if the system administrator has set permissions, the business owner can decide who has access to which resources.
To gain access, all that is needed are the correct credentials. One major downside of the DAC system is that it relies on the end-user to control security levels, which can result in oversight or errors.
DAC systems are frequently used in environments where users must share resources with others, such as file-sharing systems or databases.
Before a DAC system can be implemented, its administrator must identify who will be using it and what resources will be available to them. Each resource has an owner who ensures only the right people can use it. The owner then can allow or disallow specific individuals or groups access to the resource.
Users are granted access to resources in a DAC system according to their assigned roles. Access to a resource can be restricted to read-only, read-write, or other access levels.
Access control lists (ACLs), which are lists of permissions attached to each resource, are commonly used in implementing DAC systems. The DAC system verifies the identity of the requesting user against the ACL for the resource in question to grant or deny access.
Role-Based Access Control (RBAC)
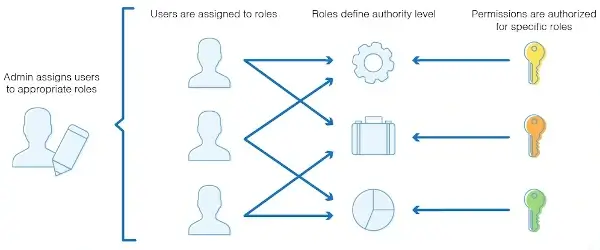
Permissions are typically assigned to users based on their organizational roles, making role-based access control (RBAC) a common form of security.
This system determines access based on role, location, and the resources required to perform a specific task.
Business owners often favor RBAC because it simplifies the division of workers into different groups with varying levels of access to resources.
For instance, workers in HR wouldn't need to know about marketing materials, and marketers wouldn't need to know about salary structures. RBAC is a flexible model that makes it easier to monitor activity and protect data from leaks and breaches.
Here's an illustration of how a company might use role-based access control (RBAC):
- The company's roles, such as "salesperson," "marketing manager," and "human resources manager," are defined by the system administrator.
- The system administrator assigns permissions to each role according to its essential resources and tasks. For example, the "salesperson" role may be able to see customer contact information and make sales reports. In contrast, the "marketing manager" role may be able to see marketing materials and create marketing campaigns.
- A new employee is assigned a role based on job responsibilities. A new salesperson, for example, would be assigned the "salesperson" role.
- When an employee tries to access a resource, the RBAC system checks the employee's role and the permissions connected to that role to see if the employee has the necessary permissions.
- If an employee's duties change, their role can be updated to reflect their new position. If a salesperson is promoted to marketing manager, their title will change from "salesperson" to "marketing manager." This would update their permissions to reflect their new role.
This is just one example of how RBAC could be used in a business. How it is implemented depends on the organization's needs and wants.
Mandatory Access Control (MAC)
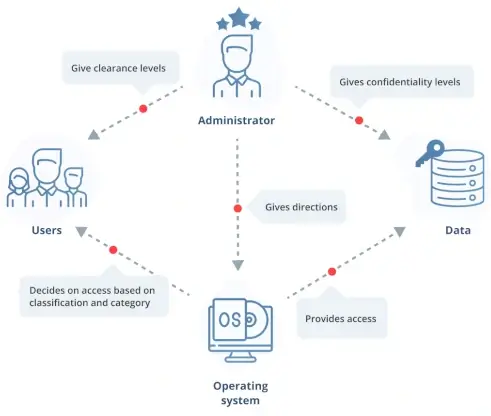
The most stringent type of access control is the mandatory access control system. System administrators are in charge of everything, and users can't change permissions or access levels independently.
Government entities widely utilize this technology because of its tight privacy safeguards.
In this access control system, users are issued unique "tags" that determine their amount of access to resources. These tags function similarly to digital security profiles based on the sensitivity of the information included in the resources.
The resource owner does not have the power to grant access to anything listed in the system. This method is highly secure and excellent at safeguarding sensitive information.
Besides being used by the government, Windows Vista and Windows 8 used a version of MAC known as "Mandatory Integrity Control" (MIC). This system applied integrity levels (IL) to the processes and files running during a login session.
An object's IL showed how much trust it would have. An IL was given to each subject and put on their access token.
The levels in MIC included low, medium, high, and system. A user couldn't access an object unless their level matched or exceeded the object's level. Windows made it so the user couldn't add or delete files with a higher IL.
First, it compared the IL, then checked the ACLs to ensure that the correct permissions were in place. This system used the Windows DAC system's Access Control Lists (ACLs) and combined them with integrity levels to make a MAC environment.
More Hands-On and More Intuitive Systems
While there are some tried-and-true methods for controlling access, advancements in technology have opened the door to novel methods. There are various ways to approach your system based on how "hands-on" or "intuitive" you intend to be with it.
That is why the following access control systems were created:
Rule-Based Access
A system that provides permissions based on, you guessed it, rules and regulations. When a user attempts to access a resource, the operating system checks the rules in an "access control list" to determine whether the user is authorized. This approach can be coupled with role-based access control and needs some work to set up.
Attribute Access Control
A more complex system that grants varied permissions based on user attributes. These attributes function as components of a user profile, determining access. Policies are based on these factors to assess whether a user should have access. These attributes are available from a different database, such as Salesforce.
Identity-Based Access Control
A system that enables or refuses access to a resource based on the user's identification. This could be done using visual or biometric data. If a user's identification matches a name on the access control list, they will be permitted access. Rather than grouping employees together, this approach is technology-driven and allows for more specific access. It also gives the business owner more control.
History-Based Access Control
A system that determines access based on a user's past security activities. It examines the user's activity history, such as the time among requests, the information requested, and the recently opened doors. For example, if a user has worked with secure accounting information for a long time, the system may flag a request to see the marketing plan for the following year.
Challenges of Access Control
Because current IT environments are increasingly distributed, with resources spread out physically and logically, access management is becoming more complex. This makes it tough to keep track of assets that are continually changing.
Specific difficulties include:
- Managing remote IT environments
- Password fatigue
- Compliance visibility
- Data governance
Typical authorization issues occur when a worker leaves a job but still has access to company assets. This leaves holes in security because the person's device is still connected to the company's internal network but is no longer being watched. To avoid this, tracking and reporting on access to protected resources and updating access control lists and permissions, as needed, is critical.
Another essential aspect of access control is user experience. If access management technology is hard to use, employees may use it incorrectly or entirely avoid it, which could lead to security and compliance problems. Also, if reporting or monitoring programs are hard to use, employees might make mistakes when using them, which could lead to security breaches.
Access Control Software

There are many different kinds of access control software and technologies, and they are often used together as part of a larger strategy for identity and access management (IAM).
They focus primarily on a company's internal access management or its customers' access management.
The idea of keeping your resources safe will never get old, but access control has changed from keeping physical documents safe in buildings to using cloud-based platforms. As our technological prowess improves, so does our flexibility, which is why we created different security services for our clients.
Our web-based remote monitoring services watch over your servers and network components, websites, online applications, and email infrastructure around the clock every day of the year.
We ensure all your devices are online, working correctly, and serving the proper content to your clients at the right moment.
Our monitoring services can help you make your business more productive and less likely to lose revenue due to failed online transactions or any potential security breach that can affect your business and your valuable data.
X


 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.