Odds are, you've heard about the dark web. Nevertheless, you may be unsure about its threat to your business and how to address it.
The dark web is a set of anonymously hosted websites within the deep web accessible through anonymizing software, commonly "TOR" (The Onion Router). The anonymity these websites provide makes them the perfect online marketplace for illegal activities.
Many businesses have fallen victim to these illegal dealings, which are often devastating and result in substantial financial losses.
Website builders, tools used to create and design websites without extensive coding knowledge, often come with additional features and benefits, such as 24-hour customer support and robust security measures. But what about those situations where this is not enough?
Keep reading to find out more about how to avoid these threats.
What is Dark Web Monitoring?
Monitoring the dark web means searching for and keeping tabs on any mention of your company that may appear there. Monitoring tools are like search engines for the dark web.
They help you locate confidential business data that fraudsters have stolen or leaked on the dark web. This information could include compromised credentials, passwords, account information, intellectual property, and other sensitive data.
Dark web monitoring and other essential elements, such as WebOps, are vital in your security strategy, providing proactive threat detection and early warning systems.
What is WebOps? It refers to the operational aspects of website and web application development and management and plays a crucial role in ensuring the security and functionality of your online presence. By incorporating WebOps practices into your cybersecurity strategy, you can effectively deploy, monitor, and optimize your web infrastructure, enhancing its resilience against potential attacks.
Why Does Your Business Need Dark Web Protection?
In 2020, the US suffered twice as many cyberattacks as any other country.

This alone highlights the need to protect your business and stay one step ahead of cybercriminals.
Beyond the potential financial losses incurred, successful cyberattacks also damage your company's reputation. In severe cases, it could even result in legal action and sabotage customer trust. The reality is that protecting your sensitive information with dark web monitoring software is more crucial than ever.
Besides locating information from data leaks and breaches, monitoring software classifies cybersecurity risks from unknown sources. Alerts about data breaches on the dark web can help you classify and address threats more quickly by linking mentions of your data to other threat sources.
Dark web monitoring can help you expose and mitigate the following types of breaches:
- Third-party breaches
- P2P leaks
- Data dumps on hacker forums and chat rooms
- Data leaks
- Domain spoofing
- Identity theft
Beyond that, dark web monitoring also has the following advantages:
- Early threat detection: If your data ever appears on the dark web, a monitoring tool will immediately alert you and your team so that you can take steps to limit the damage.
- Threat prevention: Monitoring the dark web can help discover potential security loopholes in your company's network. Your team will be able to assess current security measures and implement necessary changes to avoid breaches in the future.
- Employee identity theft protection: Dark web monitoring can also be applied to employee private data. This promotes employee trust and morale within the company and even protects against tech support scams that can trick unsuspecting individuals into divulging sensitive information.
- Proactive Security Posture: Implementing dark web monitoring demonstrates a proactive approach to cybersecurity. This demonstrates to your stakeholders, customers, and partners that you are serious about the security of their data and will work to prevent any threats that may arise.
- Compliance and Regulatory Requirements: Dark web monitoring can help you meet compliance obligations and industry regulations. You can demonstrate compliance with regulations such as GDPR and HIPAA by actively monitoring for data breaches.
How Does Dark Web Monitoring Protect Your Business?

Monitoring solutions provide several possibilities for eliminating potential dangers for your company on the dark web.
Here's how they protect your business:
1. Continuous Dark Web Monitoring
Monitoring tools for the dark web use complex algorithms and crawling techniques for constant server and network monitoring. By monitoring various underground marketplaces, forums, and criminal websites, these programs can determine if your company's sensitive data is being sold or traded on the dark web.
2. Real-Time Alerts
Every second counts when your company's data is found on the deep web. Real-time alerts from dark web monitoring solutions will immediately let you know if your data has been breached or compromised. Thanks to these warnings, you can take immediate action to lessen the blow and avoid any further damage.
3. Comprehensive Data Coverage
Tools for monitoring the dark web detect and report on different data sets. This includes compromised credentials, email addresses, credit card numbers, social security numbers, and other personal and financial information forms. These tools provide thorough coverage to detect data exposure risks by tracking multiple data sources.
4. Deep Web Scanning
Some advanced solutions scan the deep web and monitor the dark web. The deep web is the section of the internet not crawled by search engines, such as private websites and databases that require a password to access. Monitoring tools can find hidden dangers on the dark web that would otherwise go undetected.
5. Intelligence Reports
Many dark web monitoring services provide detailed intelligence reports on the threats they detect. These reports can help you assess risk, identify cybercriminal patterns, and develop effective security strategies to address them.
6. Integration with Security Systems
Integrated with your security infrastructure, dark web monitoring solutions will streamline your cybersecurity operations. You can strengthen your security by integrating security information and event management (SIEM) software, threat intelligence platforms, and other security tools.
How to Use Dark Web Monitoring
To prevent cyberattacks, dark web monitoring requires a strategic approach. Here's a step-by-step guide to dark web monitoring:
1. Assess Your Needs
Determine what kind of cybersecurity measures your company needs and what sensitive information needs protection. Consider what would cause the most damage if leaked.
2. Choose a Reliable Dark Web Monitoring Solution
Find a reputable dark web monitoring provider that meets your organization's needs. Think about how well it integrates with your current security setup, data coverage, real-time alerts, and what kinds of data it tracks.
3. Implement the Monitoring Solution
Deploy the dark web monitoring solution within your IT infrastructure. Make sure the tool integrates with your security systems and meets your needs.
4. Define Monitoring Parameters
Consider carefully what information you need to keep secure, then establish monitoring parameters accordingly. Email addresses, employee login credentials, financial data, and other sensitive information may fall into this category. By adjusting the monitoring settings, you can direct the tool's attention to threats most important to your business.
It's also worth noting that proper configuration of dark web monitoring tools often involves setting up YAML files to define parameters, customize monitoring settings, and establish integration with existing security systems.
5. Establish Real-Time Alerting
Configure the dark web monitoring solution to send real-time alerts if it detects a data breach or suspicious activities related to your organization. Define the notification channels and escalation procedures to ensure prompt action is taken each time.
6. Investigate and Assess Alerts
Investigate the alerts to confirm the threat's legitimacy and severity. Human analysis helps you differentiate between false positives and genuine threats to determine the appropriate response.
7. Take Remedial Actions
Create a strategy for dealing with the situation based on the level of danger posed. Possible solutions include notifying affected parties, changing passwords, increasing security, or reporting the incident to authorities.
8. Enhance Security Measures
Dark web monitoring should be part of a comprehensive cybersecurity strategy. Governments and industries worldwide are investing in new techniques to bolster their cybersecurity.
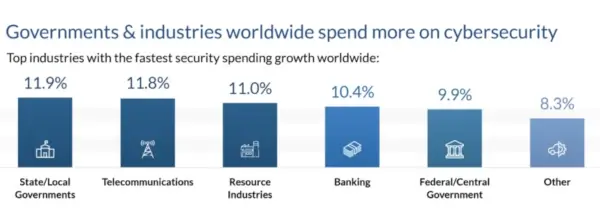
Regularly update your security measures, including employee training, strong password policies, multi-factor authentication, data encryption, and software updates. Consider incorporating robust security measures specific to your online presence, such as secure payment gateways for e-commerce platforms or implementing regular security audits.
9. Monitor and Fine-Tune
Review and adjust dark web monitoring parameters to maximize coverage and effectiveness. Monitor new threats and adapt your monitoring strategies accordingly.
10. Evaluate and Improve
Evaluate the success of your dark web monitoring efforts regularly. Assess the impact of identified threats, response times, and detection rates. Use this feedback to refine your approach and improve your overall cybersecurity posture.
Keep in mind that dark web monitoring is only one aspect of cybersecurity. To provide complete protection against evolving cyber threats, it should be combined with other preventive measures like vulnerability monitoring and a proactive security mindset.
Potential Limitations of Dark Web Monitoring
- Incomplete Coverage: The dark web is vast and constantly changing, so monitoring tools may not have access to all of it. Monitoring may be limited in hidden or inaccessible areas.
- False Positives and Negatives: Dark web monitoring tools use algorithms and automated scanning to identify threats. As a result, there is a chance of false positives (flagging non-threatening data) or false negatives (missing actual threats). Human analysis is often needed to verify and assess detected information.
- Cost and Resource Requirements: Effective dark web monitoring solutions often require investment in specialized tools, technologies, and expertise. Some organizations, especially smaller ones with tight budgets, may struggle to afford these resources.
Stay Vigilant
Cybersecurity is becoming an increasingly important issue for modern businesses. With the growing sophistication of cyber threats, organizations must prioritize implementing a comprehensive cybersecurity strategy.
Dark web monitoring can help you manage these threats and protect your company's sensitive data. Adopting a proactive cybersecurity culture is the best way to avoid the dangers of cyberattacks and keep your business running smoothly.



 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.