
Securing your company's network against online threats can seem daunting. There are so many e-commerce security threats, and it can be hard to know where to start or if you're adequately protected against them.
One important weapon in the fight for network security is your firewall. Although your firewall will remain hidden from view for most of your employees most of the time, you shouldn't forget about it. This means maintaining it, monitoring it, and testing it like any other website area. Testing site features is paramount; the same rule applies to your firewall.
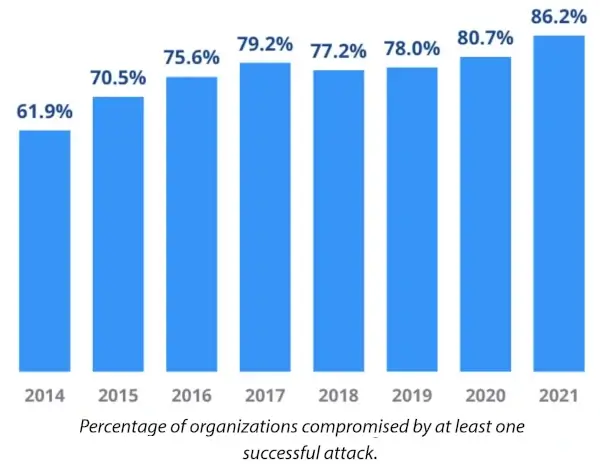
As illustrated by the graph above, your organization will likely be targeted by cybercrime at some point. So with that in mind, we're going to look at firewalls, how they can be run most effectively, and how important it is to monitor them to ensure you're as protected as possible.
What is a firewall, and how does it work?
A firewall is an essential part of any organization's network security. But simply having a firewall will not keep you safe. The firewall must be adequately monitored and maintained to ensure it works as it should.
Firewalls act as a filtration system. The firewall will scan any data packets attempting to enter the network to identify potential threats. Any data packet flagged as a potential threat will be prevented from accessing the network and potentially blocking access to some websites.
Firewalls can be software, hardware, or a mixture of both. There are many different kinds of firewalls available, the most common of which include:
- Proxy Firewall - A firewall that serves as a gateway from one network to another. Using a proxy server can have the added benefit of preventing direct connections from outside your secure network and can also provide content caching services.
- Stateful Inspection Firewall - This type of firewall allows or blocks traffic based on a predetermined set of conditions such as state, port, or protocol. It will monitor all activity whenever a connection is open. Decisions on whether to allow or block particular data packets are made based on rules determined by the firewall administrator and using information from previous connections.
- Virtual Firewalls are typically used in private or public cloud environments to monitor physical and virtual network traffic.
- Next-generation Firewall - One of the most advanced firewalls available, a next-generation firewall incorporates a sophisticated firewall alongside other threat management tools, such as integrated intrusion protection, to combat modern threats and the most advanced malware.

What is firewall monitoring?
Firewall monitoring tracks firewall metrics to ensure it runs efficiently and effectively, protecting your network. It is a common misconception that you set a firewall up and then leave it to do its job. The more closely a firewall is monitored, the more effective it will be.
Effective firewall monitoring requires some firewall monitoring tools. This lets you view how your firewall is configured and see which actions are permitted and prevented. It should also give you access to alerts, so you can see in real time when threats are identified. Finally, it should provide a way to view and analyze event logs.
The process of firewall monitoring can be as comprehensive as you wish, but you should include several actions at any level of firewall monitoring. Here are some essential steps to make up your firewall monitoring process.
- Discovery - Locate and identify all firewalls and their relevant details and assets. Having a plan or diagram to map your network can be helpful if multiple firewalls are in use; in the same way, a website wireframe might show your website's basic map and layout.
- Dashboard - Make sure you have access to a general dashboard that gives an overview of the firewall status and allows you to easily view and compare the gathered data.
- Reports - If your company developed an app and wanted to improve app retention, you would analyze consumer feedback to see what areas could improve. The same principle applies to feedback on your firewall. Ensure you can access network event logs to determine what is happening at the different stages of the threat management process. You should be able to access a deep history and see the current status where necessary. You can also periodically compare logs to look for any suspicious activity, suggesting your firewalls have been modified.
- Automation - The most efficient way to monitor a firewall is through automation. This allows problems to be spotted early and prevents them from becoming larger catastrophes. Firewalls can be configured to take specific actions in specific situations, often eliminating the need for constant physical monitoring.
Why is firewall monitoring necessary?
The effectiveness of any particular firewall will largely depend on two factors; the processing speed of the firewall and the rules governing it. Balancing speed and security is challenging when setting up and maintaining a firewall. All too often, security gaps are left, which hackers can exploit.
This is why firewall monitoring is so important. It allows you to identify and therefore plug any gaps which may have appeared in your defenses. Here are just a couple of examples of scenarios in which security breaches can occur and how firewall monitoring can fix them.
Old or redundant firewall rules
The firewall rules must be written to accommodate your specific network requirements. A simple 'deny all' setting will not work, especially as more and more employees must access the network remotely when working from home. Whenever a new access request is made for an employee working through a VPN, the firewall rules must be rewritten.

This has the unfortunate side effect of creating a long list of different firewall rules which are in effect for your network. An opportunistic hacker could use an old rule to gain access without being noticed. There are many ways to protect e-commerce sites from hacking, and including regular monitoring and removal of redundant rules will limit the risk of gaps appearing in your security.
Human Error
Human error accounts for a large percentage of data leaks. Unfortunately, it can also be responsible for firewall breaches. Hackers can steal employees' credentials who have access to your network, then use them to gain access. This can be done through malware, phishing, or other nefarious means.

Regular firewall monitoring can limit the risk by identifying anomalous access attempts to the network. Tracking access can highlight potential threats by flagging employee credentials that have attempted to access programs or data they are not authorized for.
Sometimes breaches can be wholly innocent and just down to simple mistakes. These can be limited by having clear firewall policies for your organization and ensuring all employees are familiar with them. Try looking at your company's process versus procedure regarding firewalls, and ensure both are being followed correctly.
Best practices for firewall monitoring
Firewall monitoring can be a convoluted and lengthy process if not managed effectively. Here are a few tips which should help streamline the process.
1. Take advantage of firewall monitoring tools
Firewall monitoring tools are precisely what they sound like; tools designed to help you monitor your firewall. They have been specifically designed to make the job as simple as possible, so make good use of them wherever possible.
Monitoring software will give you easy access to event logs, security alerts, and configuration settings, so you can quickly and easily search for anomalies or potential threats. This will make vulnerability monitoring much easier.
2. Test your firewall
Test your firewall to ensure any changes have been implemented successfully and provide a secure environment. This can be done like you would use smoke testing to check a piece of software.
Ensure all traffic is heading where it is supposed to without error, that any unwanted traffic is being filtered and flagged, and that appropriate logs are generated.
3. Block traffic by default
Although it may seem counterproductive initially, blocking all traffic coming into your secure network as standard can be helpful. Instead, only allow specific traffic into the areas required, such as for an online video caller for employees working remotely.
This can help prevent unauthorized access. If any of your employees' credentials are hijacked, it will mean the hackers only have access to a smaller number of systems before they alert you to their presence, limiting the damage they can cause.
Alongside this, limiting the ability to change firewall configurations to only a select few employees will reduce the risk of accidental or unauthorized changes being made to the firewall. User profiles and unique login credentials can further help with this and help you identify any problems when searching event logs in the event of a breach.

Get monitoring those firewalls
So now you should have a good idea about the importance of firewalls for your network, why they need to be monitored, and how to do it most effectively.
Be sure to invest in functional firewall monitoring software to help make the process as easy as possible. Look into automation where you can to make the process as quick as possible, too.
Please pay close attention to event logs, and make them comprehensive and easily accessible to help you look back at potential security breaches. Keep firewall testing at the forefront of your mind as you would with any other manual software testing.


 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.