The capacity to scale and process high data traffic by monitoring appliances is critical for organizations aiming to enhance or improve their security and protection from external threats. Excessive incoming traffic demands high monitoring capabilities as it overwhelms the monitoring tools and places computational bounds that increase exponentially.
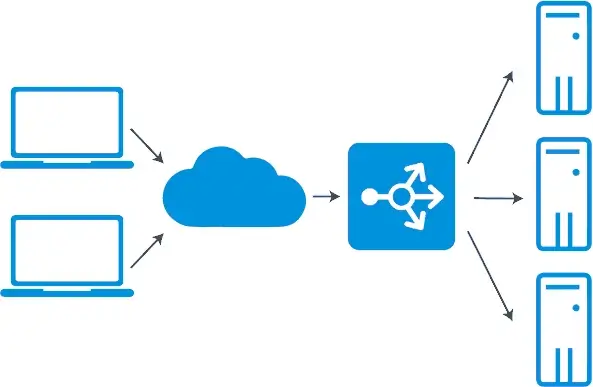
To maximize the monitoring capabilities of your security tools, scaling out is an effective way to distribute the monitoring load into the tools pool. The rise of application delivery controllers (ADCs) has revolutionized load balancers by covering application services like caching, compression, web application firewalls, and other security-relevant services.
By far, load balancing (LB) is the best method for evenly distributing application or website traffic across multiple servers to prevent them from overloading. Since load balancing works as a router, it is an effective solution for optimizing hardware and software performance with an additional layer of defense by providing application security.
For example, if your cloud calling application processes the user's credit card details, load balancing will simplify compliance with the Payment Card Industry Data-Security Standard (PCI-DSS).
Similarly, load balancers optimize security for your artificial intelligence (AI) applications by coordinating incoming data traffic rates with the capacity and number of in-placed security monitoring tools. Here are some ways to utilize load balancers for scaling your application or web service availability, resilience, and scalability with additional security.
Automate Actions
The manual implementation of load balancing is a labor-intensive task. It is a recursive process in which client usage or network traffic fluctuates over time. Manual management of the server's resources requires continuous on-demand analysis, capacity prediction, and performance evaluation. Furthermore, administrators must manually stop and restart web servers or monitoring tools when significant workload changes occur.
This type of manual load balancing requires complex interconnected predictions with a risk of potential miscalculations. Load balancing offers a high scalability feature by assigning an acceptable workload level to the pool of tools.
Similarly, automated load balancing offers sufficient resources for the immediate distribution and redistribution of traffic to improve productivity during an overwhelming workload. The automatic I/O balancing feature dynamically shifts the workload between tools over time and mitigates any issues relevant to workload imbalances. This avoids a single point of failure by preventing an individual tool from excessive monitoring.
You can dynamically assign network traffic to the monitoring tools via dynamic load-balancing algorithms. These load-balancing algorithms are categorized into various types, including:
- Geolocation-based
- Round robin
- Resource-based
- Weighted-least connection
- Least-connection
The dynamic management of incoming I/O traffic relieves IT administrators from manually adjusting monitoring tools based on a preset threshold. Hence, automation is one of the most fundamental features of scalable load-balancing tools to optimize performance.
Prevent Performance Erosion
Besides improving system performance with automated scaling, load balancing offers several other ways to optimize cybersecurity or monitoring tool performance. An effective way to process large data traffic with limited-capacity tools is to deploy multiple small-capacity tools instead of a single high-cost tool. Load balancing will enable even distribution of traffic between them for load processing.
So even if one of the security tools outbounds its computational capacity or if the traffic increases, you can include more cybersecurity or monitoring tools as per your requirements.
Load balancing also offers another feature of SSL offloading to improve performance and enhance network security.
SSL Offloading
Secure Sockets Level (SSL) encryption and decryption of network traffic is a resource-intensive task that drains server resources. SSL offloading removes the overhead by transferring the traffic to a dedicated server. It relieves the servers from the additional burden of the encryption and decryption process.
SSL offloading integration in load balancers is now a required capability, referred to as SSL load balancers. They work as server-side SSL endpoints for client connections to decrypt requests and encrypt web server responses.
The SSL offloading feature liberates the application servers from computational strain to prevent performance erosion and efficient task delivery. Furthermore, the application load balancers feature secure IP addresses of the back-end servers by supporting client SSL session termination.
Advanced Redundancy Schemes
Network or security monitoring tool failure is not an uncommon event. An unprecedented site outage can occur due to distributed denial-of-service (DDoS) attacks or operational failure, among many other causes. Such a scenario requires the presence of continuous levels of resilience.
Failover is one such practice to optimize cybersecurity and ensure device availability. The concept often goes hand in hand with load balancing. It limits the damage of a downtime tool and improves fault tolerance.
To maintain resilience in the face of natural/operational disasters or DDoS attacks, load balancers support advanced redundancy schemes. Business continuity plans can also incorporate applications like VoIP and VPNs. So the best VPN for gaming may also provide the necessary redundancy to keep your company's processes uninterrupted despite disruptions.
Since dynamic load balancers continuously monitor the server's health, they ensure device availability by distributing traffic across multiple tools. Similarly, multiple load balancing policies per device can also contribute to failover.
Implement failover or advanced redundancy schemes to optimize security tools monitoring by transferring workload to another monitoring tool if one of them fails. While following the n+1 advanced redundancy scheme, distribute the traffic in n+1 security monitoring tools. When one of them fails to monitor, distribute the traffic to the remaining n tools.
Distributing or redistributing traffic processing responsibility among the tools also enables security tools/device maintenance while performing security monitoring services in the network. The degree of redundancy is relevant to the company's criticality and affordability. Hence, some may decide to add multiple load balancers for near-zero downtime.
Upgrade Network Infrastructure
Load balancing also optimizes easy expansion of network infrastructure. For instance, if the organization plans to expand the network infrastructure from 1-10Gb or 10Gb to 40/100Gb, the load balancers can easily be configured to suspend or preclude the up-gradation of the network or monitoring tools. The expansion in the network infrastructure impacts the speed and feed of incoming traffic. This requires load-balancing configurations for flexibility in website security and network management.
It's also necessary for companies to anticipate possible network expansion before choosing a load-balancing solution. Upgrading network infrastructure requires a solution that manages pool members centrally and remotely, with a scalable load-balancing infrastructure that maintains tools' performance as the network grows.
Combating DDoS Attacks
Load balancing has played a significant role in combating cyber threats as companies have moved to the cloud. However, cloud infrastructure is at continuous risk of DDoS attacks aiming to exploit its scalability feature. This rising threat of DDoS results from exploiting many insecure internet of things (IoT) devices.
To protect against multi-vector attacks, organizations need a multi-layer defense approach that constitutes multiple strategies and controls at different network locations. The multi-dimensional security approach protects the network from attackers entering the system. Hence an attacker exploiting flaws in the first layer of defense will also have to penetrate another defense layer.
Load balancing is one such control ideally suited for a defense-in-layers model. Software-based load balancers offer an offloading feature that provides a cost-effective way to efficiently transfer the attack traffic from the company's server to a cloud service provider.
Elastic Load Balancing Against DDoS
Cloud best practices incorporate using elastic load balancing (ELB) to optimize DDoS resilience. The scaling capability of ELB reduces the impact of unanticipated excessive traffic due to DDoS by distributing it across the back-end servers. Moreover, depending on the application, we can consider different types of ELB load balancers. For example:
- Application load balancers (ALB) distribute traffic or define routes based on the content and only consider well-formed requests. ABL best protects web applications from Syn and UDP reflection DDoS attack types. It protects against these attacks by automatically scaling and absorbing additional traffic.
- Network load balancers (NLB) are best suited to protect TCP-based applications from DDoS attacks by filtering out invalid connections.
WAF and IPS Integration
Initially, the main target of DDoS attacks was the OSI model's infrastructure layer (layers 2-4). They were simple network flooding attacks aiming to disrupt service access. However, better infrastructure-level protection at layers 2-4 against DDoS attacks has diverted attackers' operations toward the upper layers of the OSI stack. Defense against DDoS attacks at an application layer is much more challenging to implement than at an infrastructure layer.
Integrating an intrusion prevention system (IPS) and web application firewall with load balancers adds another layer of protection against application layer-focused DDoS attacks. The AWS web application firewall protects applications running behind application load balancers from DDoS and other known attacks. Similarly, the Kemp LoadMaster load balancer provides a stack with SSL encryption, WAF, and IPS/IDS to secure applications from common attack vectors.
Final Thoughts
Companies should incorporate various vulnerability monitoring and attack identification/prevention tools to secure their network or outsource their services. This necessitates a solution that rigorously maintains the excessive incoming traffic concerning security tools' capabilities.
Load balancing inclusion and integration with other security tools significantly enhances their monitoring capabilities and provides better security overall against cyber attacks. Incorporating load balancing is ideal for optimizing the monitoring performance of these tools.


 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.